Guide to Identity and Access Management
Catalog
What Is Identity and Access Management?Key Functions of IAMComponents of Identity and Access Management (IAM)Benefits of IAMFrequently Asked Questions: Related ArticleWhat Is Identity and Access Management?
IAM, or Identity and Access Management, is a framework of policies and technologies for ensuring that the right individuals have appropriate access to resources within an organization. It's a critical component of information security and risk management. Here's a breakdown of what IAM entails:
1. Authentication: The process of verifying who someone says they are, typically through a username and password, but also increasingly through more secure methods like multi-factor authentication (MFA), biometrics, or single sign-on (SSO).
2. Authorization: Once a user's identity is confirmed, IAM systems determine what resources that user is allowed to access based on their role, responsibilities, and other attributes.
3. Access Control: This involves the policies and mechanisms that enforce who can access what within an organization. It can be rule-based or attribute-based, and it ensures that access is granted according to the principle of least privilege, where users have only the access necessary to perform their job functions.
4. Account Management: This includes the creation, maintenance, and de-provisioning of user accounts across all systems and applications within an organization.
5. Audit and Compliance: IAM systems track and record access and usage of resources, which is crucial for compliance with regulations and for detecting and investigating security incidents.
6. Federated Identity Management: This allows users from different organizations to access systems across organizational boundaries while maintaining a single identity.
7. Risk-Based Access Control: This involves dynamically adjusting access based on the risk profile of the user, the sensitivity of the resource, and the context of the access request.


What Is IAM?
Key Functions of IAM
1. Identity Governance: This function oversees the lifecycle of user accounts, including the assignment and management of permissions and roles.
2. Access Management: It oversees the enforcement of unified access policies, often integrating Single Sign-On (SSO) and enabling Multifactor Authentication (MFA) to enhance security.
3. Directory Services: This involves the centralized management and synchronization of user credentials across different systems.
4. User Provisioning: This automates the process of creating and configuring new user accounts, ensuring efficiency and accuracy.
5. Identity Analytics: It uses machine learning to monitor for and prevent suspicious activities related to user identities.
6. Single Sign-On (SSO): It simplifies user access to various services by consolidating multiple passwords and credentials into a single account.
7. Multifactor Authentication (MFA): It adds an extra layer of security by requiring secondary forms of authentication beyond just a password or PIN.
8. Risk-based Authentication: It employs algorithms to assess the risk associated with user actions, flagging and mitigating actions that are deemed to be high risk.
9. Identity Governance and Administration (IGA): This function helps to mitigate the risks associated with over-privileged access by carefully controlling and auditing entitlements and access rights.


Key functions of IAM
Components of Identity and Access Management (IAM)
1. Authentication
This process involves confirming the identity of individuals by checking their unique identifiers and credentials. It may include methods such as usernames, passwords, biometrics, or electronic tokens like smart cards. Authentication can also involve the use of digital certificates and multifactor authentication (MFA) to enhance security. If the provided credentials are valid, the user gains access to the resources within their designated permissions. The system may also log user activities and control access based on time constraints.
2. Authorization
This component is about granting permissions to access specific tools and resources. While authentication establishes who a user is, authorization defines what they can do. It differentiates the access levels between different users and is often associated with role-based access control (RBAC) within IAM systems. This framework is essential for setting boundaries on user operations and ensuring that permissions are enforced according to the user's role.
3. Administration
This part of the IAM system oversees the management of user accounts, groups, permissions, and password policies. It is responsible for the secure creation and modification of user accounts, enforcing strong password practices, and prompting periodic password changes to prevent security breaches. Administration serves as the backbone for other IAM components, facilitating the enforcement of authorization and authentication. It is responsible for assigning permissions to groups and users, which are then enforced by the authorization component.
4. Auditing and Reporting (A&R)
While the other components focus on user account management and access control, A&R is concerned with monitoring how users utilize their granted access. It involves tracking and detecting any unauthorized or suspicious activities by examining and documenting user access logs and security events. A&R is essential for maintaining accountability and providing insights into user behavior within the system.
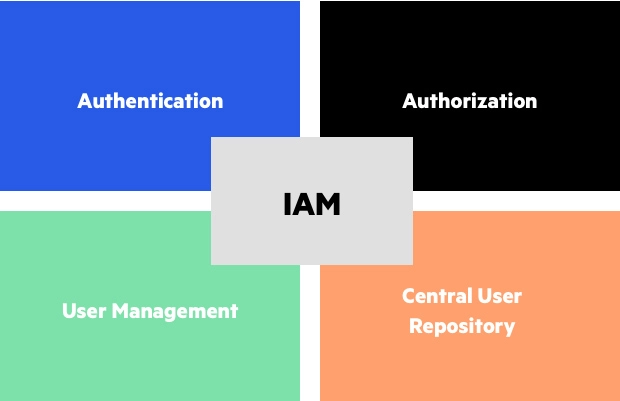

Components of Identity and Access Management (IAM)
Benefits of IAM
1. Policy Enforcement and Auditing
IAM ensures that access privileges are aligned with predefined policies, and it provides a mechanism to authenticate, authorize, and audit all individuals and services. This standardized approach helps maintain consistency and accountability across the organization.
2. Risk Reduction
Proper IAM practices give companies greater control over user access, which is crucial for mitigating the risk of data breaches from both internal and external threats. By limiting access to only what is necessary, the potential attack surface is reduced.
3. Operational Efficiency
Automating IAM processes can significantly reduce the manual effort, time, and costs associated with managing network access. This automation streamlines the workflow and allows IT teams to focus on more strategic tasks.
4. Security Enhancement
An IAM framework simplifies the enforcement of user authentication, validation, and privilege policies. It also helps in managing and addressing privilege creep, which is the gradual accumulation of access rights over time that can lead to security vulnerabilities.
5. Regulatory Compliance
IAM systems facilitate compliance with government regulations by ensuring that corporate information is properly managed and not misused. They also support the ability to provide audit-ready data upon request, which is essential for demonstrating compliance with data protection laws.
6. Competitive Advantage
By implementing IAM tools and adhering to best practices, companies can extend secure access to external users such as customers, partners, contractors, and suppliers across various platforms, including mobile, on-premises, and SaaS applications. This not only enhances security but also promotes better collaboration, productivity, and efficiency, leading to reduced operational costs.


Benefits of IAM
Frequently Asked Questions:
1. Is IAM considered cybersecurity?
Yes, IAM is a critical component of cybersecurity. It encompasses the practices and technologies used to ensure that only authorized individuals can access an organization's systems and data. By managing user identities and their access rights, IAM helps to prevent unauthorized access and protect against cyber threats.
2. What is IAM and its purpose?
IAM stands for Identity and Access Management. Its purpose is to secure access to an organization's resources by controlling who can access what, and under what conditions. It aims to balance the need for secure access with the convenience of user experience, ensuring that only authorized users can perform actions within their permitted scope.
3. What is an example of IAM?
An example of IAM in action is when a user attempts to log into a corporate email system. The system will prompt for a username and password, verify these credentials against a stored database, and then grant access if they match. This process ensures that only authenticated users can access their email, preventing unauthorized access.
4. Is identity and access management a good career?
Yes, IAM can be an excellent career choice. As organizations increasingly prioritize cybersecurity, the demand for IAM professionals is high. IAM specialists can expect career growth, with opportunities to advance into roles such as Security Architect, Cybersecurity Director, or Chief Information Security Officer (CISO).
5. Is IAM a database?
IAM is not a database itself, but it often interfaces with databases to manage user credentials and access rights. IAM systems use databases to store and retrieve information about users, their roles, and permissions, which is then used to control access to resources.
6. Why do we need identity and access management?
IAM is necessary to safeguard sensitive data and resources from unauthorized access. It helps organizations maintain the confidentiality, integrity, and availability of their information assets by ensuring that only authorized individuals can access or modify critical data.
Related Article
TPS62065DSGR: High-performance buck converter, optimized power management solutions
Moisture Sensors: The Key to Smarter Soil and Water Management
STTH1R06A: High Efficiency Ultra-Fast Recovery Diode for Optimized Power Management
Subscribe to JMChip Electronics !